First published: 23 Sep 2024
Last modified:
Author CKA: Vincenzo Tagliavia (CKA, CKAD, CKS)
This article gives you a high-level view of our internal processes to secure your Kubernetes cluster. In case you’ve missed it, we wrote about Kubernetes Security Best Practices in a recent blog article so head over there in case you need a refresher.
If you know how to set up and harden your cluster, Kubernetes isn’t less secure than any other technology in the marketplace.
For years, top security consultants – RedHat, Aqua, Sysdig, etc – have placed cluster misconfigurations as one of the main reasons Kubernetes security breaches happen in the first place. Kubernetes misconfigurations are preventable when you possess the know-how and prioritize security in your organization. Therefore, the deeper your knowledge around default configuration values and gotchas, the better your awareness and security posture will be.
At a Glance:
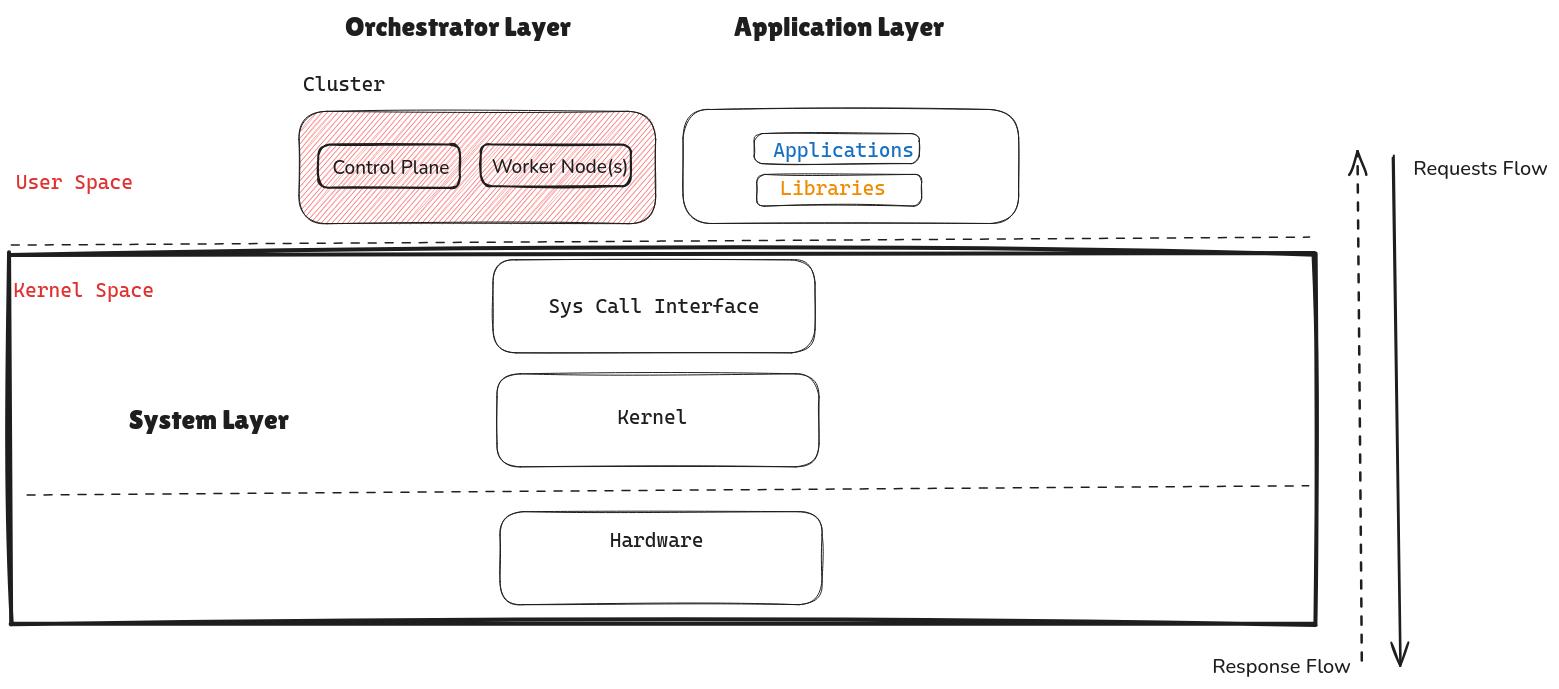
Default Settings: Beside being the most popular container orchestrator, Kubernetes’ main purpose is speed of developments and deployments. However, there is a cost to pay for that speed, and default configurations often grant excessive permissions you need to be aware of.
Human Errors: “Errare humanum est”; human beings can make errors and it is OK. Preventing these errors with automated tests and the right processes in place is doing something about it.
Supply Chain Vulnerabilities: Kubernetes security isn’t just about Kubernetes. We need to look beyond the orchestration layer and think more deeply about the inputs/outputs across the supply chain. For instance, registries, container security, development practices, distribution of images and binaries, and so on; these are all important aspects of security we often miss.

Securing your Kubernetes cluster involves a number of sequential – and at times concurrent – steps:
Analysis of business and technical requirements
Inspect Monitoring and observability tools to identify potential issues in terms of utilization, saturation, errors and latency (Golden signals of SRE Observability)
Installing one or more security forensic tools that are compatible with your needs. These security binaries (if you want to install them at the Operating System level via a package manager or from source) run mostly static scans of configuration files, manifests and more. Dynamic scans are also possible for ports and other cluster components at runtime. Note that some tools may be used also via Kubernetes Jobs without installing and then managing the package at system level.
Implement scan reports manually and plan scripts or other tools to automate this process in the long term.
Our Kubernetes security consultants bring a wealth of expertise and experience to ensure your clusters are secure:
Expertise: Our team comprises seasoned professionals with deep knowledge of Kubernetes security best practices.
Customized Solutions: We tailor our security strategies to meet your specific needs and industry requirements.
Proactive Approach: We focus on preventing security issues before they impact your operations.
Comprehensive Services: From security assessments to incident response planning, we offer a full spectrum of services to safeguard your Kubernetes environment.
Continuous Support: Security is an ongoing process. We provide continuous monitoring and support to keep your clusters secure.
Kubernetes security is a critical aspect of managing containerized applications. By understanding the inherent vulnerabilities and common security issues, and by implementing robust security measures, you can protect your Kubernetes clusters from potential threats. Leveraging the expertise of our Kubernetes security consultants ensures that your environment remains secure, compliant, and resilient against emerging threats.
Schedule Your Free 30-Minute Consultation Now
Unlock expert insights tailored to your needs with a no-obligation, 30-minute consultation. Contact us now to see how we can help you optimize your Kubernetes setup and reduce inefficiencies.